Acls questions and answers pdf – Welcome to the world of ACLs! This comprehensive PDF guide, “ACLs Questions and Answers,” is your go-to resource for understanding the ins and outs of Access Control Lists. Dive in and discover the power of ACLs to enhance the security of your systems.
From types of ACLs to best practices and real-world case studies, this guide covers everything you need to know about ACLs. Get ready to master the art of access control and secure your systems like a pro!
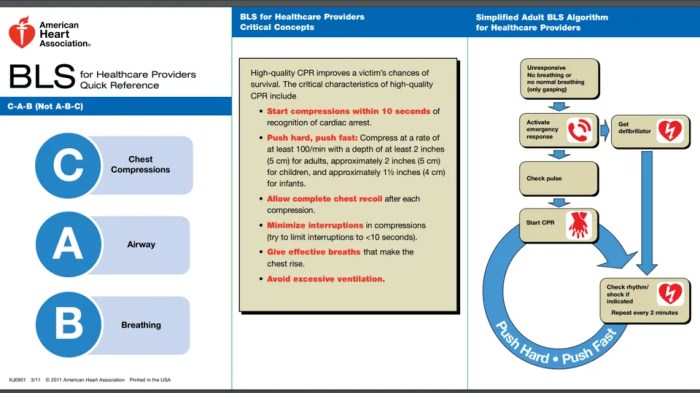
ACLs Overview
Access Control Lists (ACLs) are a fundamental mechanism used in computer systems to manage access permissions for users and groups. They provide a flexible and granular approach to controlling who can access specific resources, such as files, folders, and network services.
ACLs are beneficial because they allow administrators to tailor access permissions to meet the specific requirements of their systems. This enables them to grant or deny access to specific users or groups based on their roles, responsibilities, or other criteria.
ACLs also provide a centralized way to manage permissions, making it easier to maintain and enforce access control policies.
Types of ACLs
Access control lists (ACLs) are mechanisms that regulate access to resources within a computer system. They define who can access a resource and what operations they are permitted to perform. Different types of ACLs exist, each with its own characteristics and applications.
ACLs can be broadly categorized into two main types: discretionary ACLs (DACLs) and system ACLs (SACLs).
Discretionary Access Control Lists (DACLs)
DACLs are the most common type of ACL. They allow the owner of a resource to explicitly grant or deny access to specific users or groups. DACLs are typically used to control access to files, folders, and other resources on a file system.
For example, a DACL might grant read access to a file to a group of users called “Sales” and deny write access to all other users.
System Access Control Lists (SACLs)
SACLs are less common than DACLs. They are used to control access to system objects, such as processes, threads, and registry keys. SACLs are typically used to enforce security policies or to protect sensitive system resources.
For example, a SACL might grant the “System” user full control over a process, while denying all other users any access.
ACLs Implementation

ACLs are implemented in various systems through a combination of hardware, software, and firmware components. The specific implementation details vary depending on the system, but the general principles remain the same.
In hardware, ACLs are often implemented using dedicated circuitry that performs access control checks in real-time. This hardware-based implementation provides high performance and low latency, making it suitable for high-volume environments.
In software, ACLs are typically implemented as part of the operating system or application software. The software checks access permissions based on the ACLs defined for the resources and the user’s credentials. This software-based implementation provides flexibility and allows for more complex access control rules.
For a comprehensive understanding of ACLS questions and answers, explore the story of Henry Lowe , the renowned debater who championed the art of rhetoric. His legacy inspires us to seek knowledge and excel in the realm of critical thinking.
Returning to the topic at hand, the ACLS questions and answers PDF remains an invaluable resource for those seeking to master this essential medical skill.
In firmware, ACLs are often implemented as part of the device’s firmware. This firmware-based implementation provides a balance between performance and flexibility, making it suitable for embedded systems and other resource-constrained environments.
Best Practices for Implementing ACLs
There are several best practices to follow when implementing ACLs:
- Use a consistent approach:Implement ACLs consistently across all systems and applications to ensure a uniform level of security.
- Use the principle of least privilege:Grant users only the minimum level of access necessary to perform their tasks.
- Review ACLs regularly:Regularly review ACLs to ensure they are up-to-date and reflect the current security requirements.
- Use audit logs:Enable audit logging to track access attempts and identify any suspicious activity.
- Use role-based access control (RBAC):Use RBAC to simplify ACL management by assigning users to roles with predefined permissions.
ACLs Management
ACLs management involves creating, modifying, and deleting ACLs to ensure the desired level of access control is maintained. This section provides guidance on managing ACLs effectively.
ACLs can be managed through various methods, including command-line interfaces (CLIs), graphical user interfaces (GUIs), and programmatic interfaces (APIs). The choice of method depends on the operating system, the specific ACL implementation, and the user’s preference.
Creating ACLs
- Identify the resource or object for which an ACL needs to be created.
- Use the appropriate command, GUI, or API to create an ACL for the specified resource.
- Specify the access control entries (ACEs) that define the permissions to be granted or denied.
- Verify that the ACL is created successfully and the desired permissions are applied.
Modifying ACLs
- Identify the ACL that needs to be modified.
- Use the appropriate command, GUI, or API to modify the ACL.
- Make the necessary changes to the ACEs, such as adding, removing, or modifying permissions.
- Verify that the ACL is modified successfully and the desired permissions are applied.
Deleting ACLs, Acls questions and answers pdf
- Identify the ACL that needs to be deleted.
- Use the appropriate command, GUI, or API to delete the ACL.
- Verify that the ACL is deleted successfully and the resource is no longer subject to its access control rules.
ACLs Auditing: Acls Questions And Answers Pdf

Auditing ACLs is crucial for maintaining network security and compliance. It involves regularly reviewing and assessing ACL configurations to ensure they align with security policies and prevent unauthorized access to network resources.
Techniques for Auditing ACLs
- Log Analysis:Examining system logs for events related to ACL changes, such as modifications, additions, or deletions, can provide insights into ACL activity.
- Vulnerability Scanners:Using vulnerability scanners to identify potential ACL misconfigurations or weaknesses can help detect vulnerabilities that could be exploited by attackers.
- Network Traffic Analysis:Monitoring network traffic can help identify suspicious patterns or anomalies that may indicate unauthorized access or ACL bypass attempts.
- Configuration Management Tools:Employing configuration management tools to track ACL changes over time can help identify unauthorized modifications and ensure compliance with security policies.
- Manual Review:Periodically reviewing ACL configurations manually can help detect errors, inconsistencies, or unauthorized changes that may have been missed by automated tools.
ACLs Case Studies
ACLs have been used in various real-world scenarios to enhance security. Let’s explore some case studies to understand how they’ve been implemented and the challenges faced.
Case Study 1: Enhanced Network Security
In a large enterprise network, ACLs were implemented on routers and firewalls to restrict unauthorized access to critical resources. By defining specific rules, the network administrators were able to:
- Prevent external attackers from accessing internal servers
- Limit employee access to specific applications and websites
- Control traffic flow between different network segments
The implementation of ACLs significantly reduced the risk of network breaches and ensured compliance with security regulations.
Case Study 2: Data Protection in Healthcare
A healthcare organization used ACLs to protect sensitive patient data stored in a database. The ACLs were configured to:
- Restrict access to patient records only to authorized medical professionals
- Audit all access attempts to identify suspicious activities
- Implement role-based access control to limit privileges based on job responsibilities
By implementing ACLs, the healthcare organization ensured that patient data was protected from unauthorized access and met industry-specific security standards.
Challenges and Lessons Learned
While ACLs are a powerful security tool, their implementation and management can pose challenges:
- Complexity:Configuring and managing ACLs can be complex, especially in large networks or systems with numerous resources.
- Maintenance:ACLs require regular review and updates to ensure they remain effective and aligned with changing security requirements.
- Human Error:Misconfigurations or errors in ACL rules can lead to security breaches or disruption of access.
To mitigate these challenges, organizations should follow best practices such as:
- Using automated tools to manage ACLs
- Conducting regular security audits and reviews
- Training administrators on proper ACL configuration
ACLs Best Practices
Effective implementation and management of ACLs are crucial for maintaining data security and ensuring compliance. Here are some best practices to consider:
Benefits and drawbacks of each best practice:
Define Access Levels Clearly
Establish clear and concise access levels for different user roles. This ensures that users are granted only the minimum necessary permissions to perform their tasks, reducing the risk of unauthorized access.
Benefits:Enhanced security, reduced risk of data breaches.
Drawbacks:May require frequent updates as user roles change.
Implement the Principle of Least Privilege
Grant users only the minimum level of access required to perform their job functions. This limits the potential impact of a security breach by reducing the amount of data that can be accessed by unauthorized users.
Benefits:Improved data security, reduced risk of data loss.
Drawbacks:May require additional administrative effort to manage multiple access levels.
Use Groups and Roles for Access Management
Assign users to groups or roles based on their job functions and access requirements. This simplifies access management and reduces the need for individual ACL assignments.
Benefits:Efficient access management, reduced administrative overhead.
Drawbacks:May require regular maintenance to ensure group membership is up-to-date.
Review and Audit ACLs Regularly
Regularly review and audit ACLs to ensure they are still aligned with business requirements and security policies. This helps identify and address any vulnerabilities or unauthorized access.
Benefits:Improved security posture, reduced risk of data breaches.
Drawbacks:Can be time-consuming and may require additional resources.
Document ACLs and Access Policies
Document all ACLs and access policies in a centralized location. This ensures that all stakeholders have access to the information and can understand the security controls in place.
Benefits:Improved transparency, reduced risk of misunderstandings.
Drawbacks:Requires ongoing maintenance to keep documentation up-to-date.
Use ACL Management Tools
Utilize ACL management tools to simplify the process of creating, managing, and auditing ACLs. These tools can automate tasks, reduce errors, and improve overall efficiency.
Benefits:Improved efficiency, reduced administrative overhead.
Drawbacks:May require additional investment in software and training.
ACLs Resources
This section provides additional resources on ACLs, including links to relevant articles, white papers, and tools.
These resources can help you learn more about ACLs and how to use them effectively in your environment.
Articles
- Access Control Lists (ACLs) (Microsoft)
- Understanding ACLs (Cisco)
- Access Control Lists (ACLs): What They Are and How They Work (Imperva)
White Papers
- Identity and Access Management (IDM) Solution Overview (Cisco)
- Active Directory Rights Management Services (AD RMS) Technical Overview (Microsoft)
- VMware Access Control Solutions for Hybrid Cloud (VMware)
Tools
- ACL Manager (Microsoft)
- ACL Reporter (ManageEngine)
- NetWrix ACL Monitor (NetWrix)
FAQ Summary
What are ACLs?
ACLs (Access Control Lists) are mechanisms that define who can access specific resources and what actions they can perform on those resources.
Why use ACLs?
ACLs provide granular control over access to resources, allowing you to tailor permissions based on individual users or groups, enhancing security and data protection.
What types of ACLs are there?
There are various types of ACLs, including Discretionary Access Control Lists (DACLs) and Role-Based Access Control Lists (RBACs), each with its own advantages and use cases.
How do I implement ACLs?
ACLs can be implemented in various systems and platforms. Refer to the specific documentation for your system to learn how to configure and manage ACLs effectively.
Why is auditing ACLs important?
Regularly auditing ACLs helps ensure that access permissions are up-to-date, preventing unauthorized access and maintaining the integrity of your systems.